Quantum-Safe Encryption: Safeguarding Data For The Quantum Era
Enterprise Cybersecurity Platform
A Unified Platform to Manage Your Entire Cybersecurity Ecosystem—Tools, Processes, People, Operations, and Governance—Delivering Real-Time Threat Posture and Control.
Kavayah Platform
In Today’s Ever-Evolving Cybersecurity Landscape, Staying Ahead Of Potential Threats Is A Constant Challenge. Advanced Persistent Threats, Ransomware, And Wipers Are Just A Few Risks Organizations Must Guard Against. However, Quantum Computing Is One Of The Most Complex And Far-Reaching Challenges On The Horizon. While Not An Immediate Threat, “Collect Now, De
Preparing for Quantum Computing: The Next Frontier in Cybersecurity
In today’s ever-evolving cybersecurity landscape, staying ahead of potential threats is a constant challenge. Advanced Persistent Threats (APTs), ransomware, and destructive wipers are just a few of the risks organizations must guard against. However, quantum computing represents one of the most complex and far-reaching challenges on the horizon.
While not an immediate threat, the concept of “collect now, decrypt later” underscores the urgency of preparing for a future where current cryptographic standards may be rendered obsolete.
The Promise and Peril of Quantum Computing
Quantum computers have the ability to perform complex calculations exponentially faster than classical computers. This capability promises to revolutionize many scientific fields, including chemistry, physics, and materials science.
However, in the wrong hands, quantum computing poses a significant risk by potentially breaking today’s encryption methods and exposing sensitive data to malicious actors.
The Threat to Traditional Encryption
Current encryption protocols such as RSA and Elliptic Curve Cryptography (ECC)—commonly used in HTTPS, SSH, and IPsec VPNs—rely on the difficulty of factoring large numbers or solving discrete logarithm problems for security.
Quantum computers, leveraging algorithms like Shor’s algorithm, could efficiently solve these problems, making traditional encryption vulnerable.
While a sufficiently powerful quantum computer capable of breaking modern encryption is unlikely to appear within the next 8–10 years, this timeline is shrinking with rapid technological advances. Meanwhile, adversaries are already collecting and storing sensitive data for future decryption, highlighting the need for proactive defense strategies against post-quantum threats.
Quantum-Safe Encryption Strategies
To counteract these risks, organizations must adopt quantum-safe encryption techniques that can withstand advancements in quantum computing. Three major approaches are under active development:
-
Quantum Key Distribution (QKD): Utilizes principles of quantum mechanics to securely distribute symmetric encryption keys even across untrusted networks.
-
Post-Quantum Cryptography (PQC): Involves new cryptographic algorithms believed to be resistant to quantum attacks, such as lattice-based encryption.
Fortinet, for example, has introduced quantum-safe security solutions, integrating the NIST-approved PQC algorithm CRYSTALS-KYBER in FortiOS 7.6. Their approach also includes leveraging QKD technology through partnerships with vendors like ID Quantique to secure key exchange, supported by Fortinet’s FortiGate 4201F for network encryption and FortiTester for performance measurement.
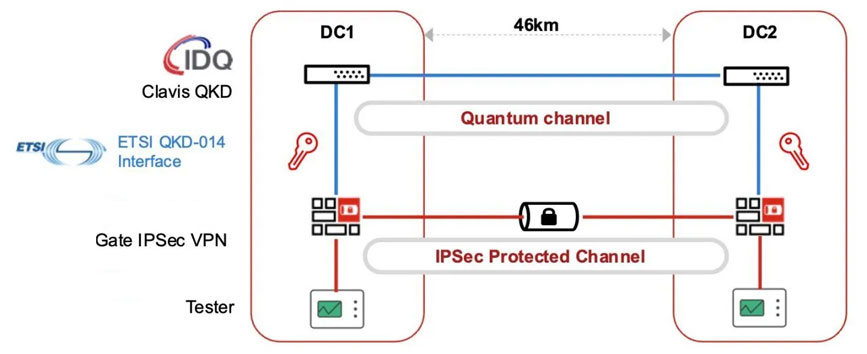
The Race for Quantum-Safe Solutions
In response to the looming threat posed by quantum computing, the global cybersecurity community is actively developing quantum-safe encryption standards.
The National Institute of Standards and Technology (NIST) is leading the Post-Quantum Cryptography Standardization Project, rigorously evaluating and selecting quantum-resistant algorithms. This initiative is crucial for enabling widespread adoption of quantum-safe encryption.
Challenges Ahead
Transitioning from traditional encryption to quantum-safe solutions is complex and presents challenges including:
-
Interoperability: Ensuring new algorithms work across diverse systems and platforms.
-
Performance Impact: Managing potential increases in computational overhead.
-
Backward Compatibility: Supporting legacy systems during the migration phase.
Organizations must carefully assess their existing cryptographic infrastructure and develop clear roadmaps to migrate toward quantum-resistant encryption.
In conclusion, while quantum computing is not an immediate threat, its transformative potential demands early preparation. Embracing quantum-safe encryption today is vital to securing sensitive information tomorrow.
Enterprise Cybersecurity Platform
A Unified Platform to Manage Your Entire Cybersecurity Ecosystem—Tools, Processes, People, Operations, and Governance—Delivering Real-Time Threat Posture and Control.
Kavayah Platform